Recent pressure for compliance with Consumer Financial Protection Bureau (CFPB) standards to secure sensitive pieces of customer information and to ascertain that non-public personal information (NPI) is secure has made it critical that, as a title and settlement provider, you know that any software that you utilize handles NPI appropriately. This means the software applications you use should ensure that sensitive data cannot be read or tampered with as it travels over the Internet to customers or external providers.
The CFPB mandates that any sensitive data that originates on computers in your office should only leave your office via a secure connection. Since many modern software applications, both web and desktop, access the Internet behind the scenes, it is important to verify with your providers that all data transmitted over the Internet uses Secure Sockets Layer (SSL). And, if you are using web software that is hosted elsewhere, you should verify that the URL begins with “https:” (note the “s” on the end) as this implies that all data that travels between your computer and that website is done securely, using SSL.
The purpose of using SSL is to increase the security of your data. This aligns nicely with ALTA’s Best Practices framework Title Insurance and Settlement Company Best Practices (Version 2.0 Published July 19, 2013) that dictates guidelines for keeping user data safe.
An SSL Certificate is essentially a key that is used to encrypt data before it is sent or received over the Internet. When users access RamQuest’s PaperlessCloser or services like Closing Market web services, via the Web, encryption ensures no one can read the data as it travels to or from the user’s computer over the Internet to the RamQuest application and database.
All SSL certificates are “signed” - a certificate is either signed by you or purchased from a third party Certificate Authority (CA), like Verisign, Thawte, GeoTrust, GoDaddy etc. To your users or customers, a self-signed certificate says “I am who I say I am” while a third-party signed certificate from Verisign, for instance, says, “I am who I say I am and Verisign agrees”.
RamQuest’s Best Practice Recommendation is that you purchase a single site SSL certificate from a third party vendor. For example, GoDaddy’s “Protect 1 Website” (about $70/year) will work to secure both RamQuest’s Closing Market and PaperlessCloser applications. We also recommend that the certificate be a 2048 bit key length (most authorities already require this). And you might consider purchasing a certificate with a longer expiration period – maybe 7 to 8 years – to avoid frequent, repeated renewals. This is the SSL certificate that you will use on your RamQuest Paperless Closer/Closing Market Web services server that is exposed to the Internet.
Our recommendation is to utilize a third-party signed certificate on your external-facing web server.
For added protection, you could also choose to have a self-signed certificate between the Web server and the App server, just in case there is some security breach that results in a break-in. A self-signed certificate is useful for links between internal servers because, while they both offer the same encrypted protection, a self-signed certificate has no cost but requires a little more maintenance than a paid, signed certificate.
Generally, the connection between the Web server and the App server does not need an SSL certificate because it is not exposed to the Internet, assuming the servers are in the correct network segments. That means that the App server is protected by a firewall between it and the Web server located in a DMZ. A DMZ (demilitarized zone) is an area outside your domain but still under your control. It is neither as secure as the internal domain network nor as unsecure as the public Internet. This is because the App server at that point is non-addressable from the public internet.
When deciding what kind of SSL certificate to implement, it is important to understand the nuances of the choice you make. For instance, while implementing a self-signed certificate is both free and secure, because it is not from a CA, using it for an external user-facing web application like PaperlessCloser will result in an annoying pop-up message that the security certificate presented by the website is not issued by a trusted certificate authority.
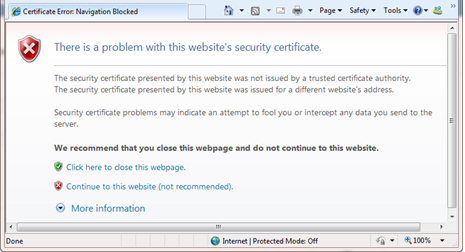
You can choose to continue to the site, but every time you access the website, you’ll encounter this message. Conversely, a self-signed certificate does not have this same effect on the Closing Market portal’s communication to your web server’s Closing Market Services because the services are not utilized as an external user interface and the communication is handled with no intervention necessary by an end-user.
Of course there are variants to consider. For instance, you may want to consider expanded SSL certificates for either multiple domains (www.mydomain.com and www.yourdomain.com ) or for wildcard sub-domains (mail.mydomain.com, portal.mydomain.com and mydomain.com).
Now is the time to begin to align with CFPB mandates and Alta Best Practices to secure your web server – begin by talking to your IT specialist to make sure you are utilizing an SSL certificate on your web server. If you need more information or assistance, contact support@ramquest.com.